Technical documentation


In business, the use of mobile devices simplifies, accelerates and optimizes business processes. However, it must be understood that the more complex the device is, the more threats it is exposed. It will be ideal if you note that the list of threats listed here isn’t complete. However, it contains a description of the basic methods for data leakage. The complete description of threat patterns can be found in the document “Mobile Security Reference Architecture,” prepared by the United States Federal CIO Council and the United States Department of Homeland Security (May 2013). The descriptive information is simplified and is only intended to introduce procedures. More detailed information or technical specifications can be found on the Internet.

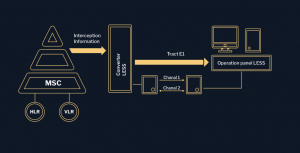
1. LESS-Law Enforcement Support System (SORM-rus.)-a system of technical means to carry out investigative and operational work.
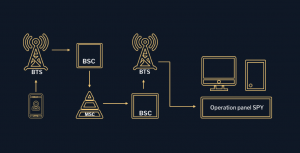
2. Service Provider (Mobile Connection Operator).
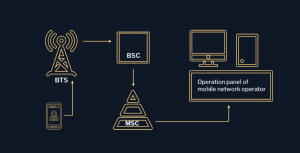
3. Operating System (OS) of mobile devices and software producers/developers.
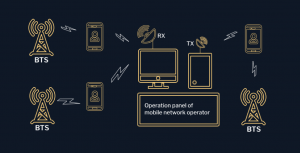
4. Radio channel traffic interception (intercept complexes: active, semi-active, passive and other interceptors).
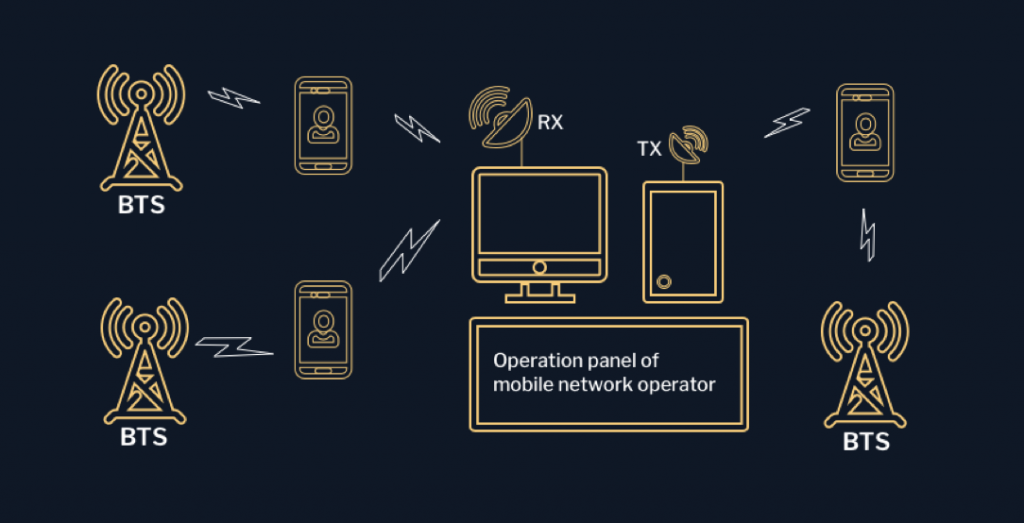
For the technical control of a mobile device or SIM, its identifiers must be known. All communication networks around the whole world are governed by state regulatory bodies and are therefore technically linked to the LESS (Law Enforcement Support System – All information on this system can be found on the Internet). IMEI (International Mobile Equipment Identity) is the main identifier of a mobile device. It passes this parameter in the network.
Public parameter, Mobile Subscriber Integrated Services Digital Number (MSISDN) – a number of digital network mobile subscribers with integrated services for GSM, UMTS, etc. This parameter is not passed in the network, but is comparable to IMSI.
These parameters are sufficient to obtain all the information necessary and to use it for analytical conclusions. The following information about a subscriber can be obtained by means of LESS, intercept complexes and other mechanisms: – By IMEI it is possible to obtain all SIM IMSI cards used in a particular device and, as a result, all SIM billing data (location, contact circle, SMS, MMS, voice, URL, login and passwords, etc.). – By IMSI, IMEIs of devices and IMSI of SIM can be obtained – cards used in these devices and therefore all the above data. VipLine billing data does not belong to any mobile operator, since VipLine SIM card does not belong to them. VipLine SIM card also has no public access to MSISDN.
The level of encryption depends on the network to which the subscriber is connected. VipLine special SIM applet notifies subscribers if the encryption level has been reduced.
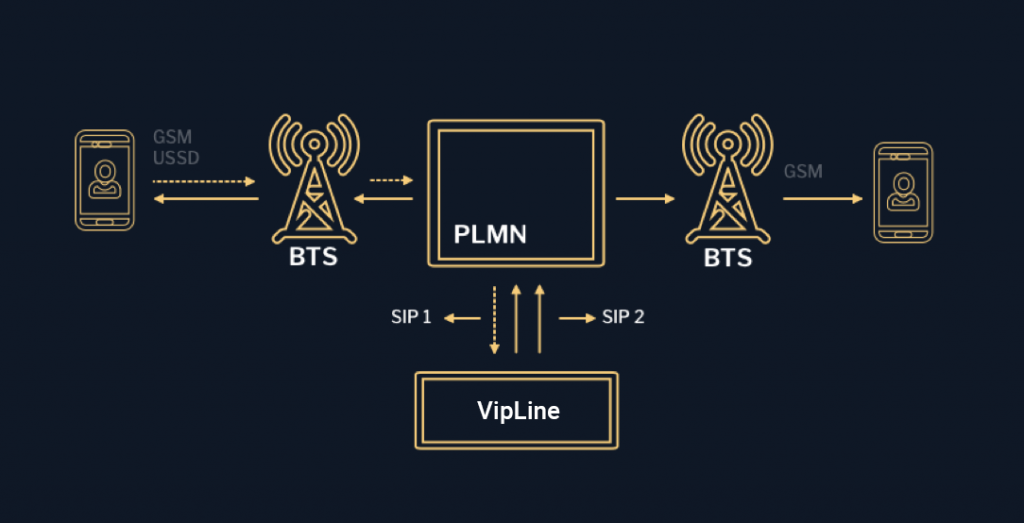
After entering the dial number, subscribers with regular SIMs press the call button. At this stage, the mobile device sends the ALERT signal to the BSS (Base Station Subsystem) via FACCH (Fast Associated Control Channel). This signal is then sent to MSC (Mobile Switching Center). MSC sends the complete message address to the calling subscriber (the calling party). The caller hears the dial tone, and the target party hears ringing sound. With the knowledge of the mobile number of subscribers A or B (MSIDIN), all call details of the subscribers involved can be obtained and the online session can even be intersected.
The VipLine subscriber presses the call button. The SIM applet intercepts the call at this stage and redirects it to our service number. The dialed number is transferred in encrypted form from the subscriber to the PBX via the signaling channel. All outbound calls are delivered to our network service numbers. The PBX further sends a call to the end user.
Call Back – The GSM subscriber to VipLine presses the call button. The call is falling at this stage. We then send the command via encrypted channel to the VipLine PBX server. VipLine PBX asks the host operator’s VLR to allocate a temporary number via SS7 to the subscriber. VipLine PBX initiates a call to this MSRN as soon as the MSRN is allocated to our SIM. As soon as subscriber A responds to the call, the leg A begins and the PBX begins to call subscriber B. When subscriber B responds to the call, the leg B begins. This call logic makes it impossible to get information about the call statistics from the billing of the host operator.
Unknown are: The operator is connected to the VipLine SIM card, the SIM MSISDN number and the MSISDN IMSI, KI and IMEI. Even if subscriber B is controlled, it is impossible to understand who was the second speaker because the session always consists of two legs and VipLine PBX is always in between. This technology makes it difficult to define your contact circle.
A call to regular SIM takes place in accordance with standard procedures. Once the call initiation procedure and TMSI assignment (Temporary Mobile Subscriber Identity) are completed in the VLR coverage area, the traffic termination begins and the session is considered to be set up. The operator’s billing stores information about the calling device, the location of the calling device during the session, the duration of the call, etc. A call to the VipLine SIM card is carried out as follows: SIM is assigned a virtual number -DID. The DID number receives a call from the network, translates it into a SIP protocol and routes it to the VipLine PBX. The VipLine PBX defines a subscriber who has the DID and starts the above-mentioned calling procedure. It is therefore impossible to define the location of the subscriber and the relationship of each subscriber, since VipLine PBX is always in between.
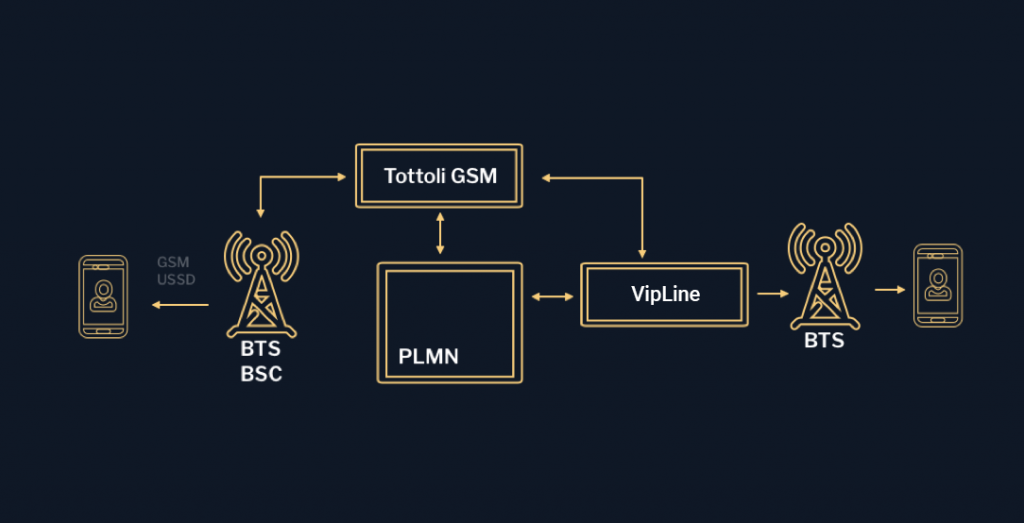
Given that public networks have standard roaming services requests, hackers have the opportunity to organize attacks in a SS7 network. These attacks appear to be regular SS7 requests from the SIM issuer operator’s HLR. The purpose of these requests is to intercept information (IMSI, KI, IMEI, etc.). HLR is an integral part of our infrastructure, so we intercept and inform our subscriber about any attacks. That’s one of the features of PING.
Taking into account the fact that operators actively develop their phonetic characteristics (voice print) of the subscriber research mechanisms. VipLine allows for both incoming and outgoing calls to distort the acoustic characteristics of the subscriber. This mechanism is very useful when calling a regular SIM card from VipLine SIM card.
Hackers use zero-class SMS to control phone functions or pre-installed applications that do not reveal themselves and do not leave footprints on the phone. Such text messages are also called Silent SMS or Stels SMS. All these requests are sent to the operator-issuer’s HLR. HLR is part of our infrastructure in our case, so we detect all such requests, block them and notify our subscribers of such attempts. This function is part of the PING mechanism.
RESUME
VipLine SIM cards do not have host operators billing, which prevents attackers from acquiring the necessary details for analytical work (contact circle, location, real identifiers, voice).
This was made possible by the incandescence of all three-level processes: A subscriber device (modified firmware phone), an identification module (VipLine SIM card with unique applets) and a network layer (full control of HLR, MSC and SMSC).P.S.
It should be noted that all phones are blackboxed proprietary devices. Nobody knows the peculiarities of the settings stored there, but the manufacturer himself, and sometimes even the manufacturer doesn’t know all the firmware bugs. It is also necessary to understand the constant improvement of monitoring tools.
Analytical tools identify single-use devices according to billing patterns: The time stamp of the first and last phone calls, the total number of calls and the average number of unique online subscribers. With access to all national operators ‘ billing systems, it is possible to determine when the subscriber has removed one phone and started calling from the other: By enabling geolocation data, the place of residence of the subscriber can be identified.
