How It Works: The Process Unveiled


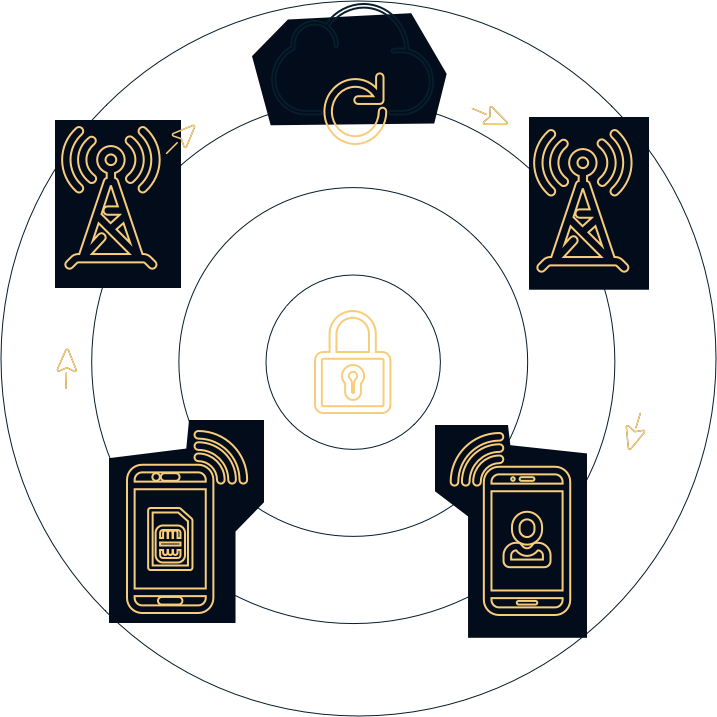
The VipLine encrypted SIM card takes privacy to the next level. Rather than obscuring the process and making our technology hard to understand, we want our customers to know how a PGP SIM works, specifically ours.
While a standard SIM does not keep your personal information secure, our anonymous SIM card makes it a priority. To clarify our technology and shed transparency on the VipLine secure SIM card difference, we have made our process public so you can stay private.
The VipLine difference that allows access to our card’s many features is best explained through a four-step process. These steps are taken as soon as you initiate the process by making or receiving a phone call.
These four steps are only possible once the VipLine secure PGP SIM is inserted into your cellular device.
Modern-day business relies on connectivity. Employer-to-employee, client-to-company, and business-to-business relationships can only be fostered with the right technology.
Unfortunately, as critical these connections are, it does not mean that smartphones for business use are safer than for personal use.
As businesses often have complex connectivity requirements and large amounts of information, the likelihood of these connections being infiltrated skyrockets. Fully understanding the threats mobile devices are exposed to can be challenging, and a failure to do so can put your company at risk.
Thankfully, VipLine has provided some of the most common paths a threat will take and the main causes of data leakage. As the list does not provide all the possible threats your business may face, you should be making an effort to identify threats and protect yourself.
The first step to safeguarding yourself from potential threats is ensuring all your business communication is done through encrypted channels using a VipLine anonymous SIM.
Understand The Threats
Encryption is used to create a randomized number that begins before your conversation starts. The servers, upon dialing, randomize your number and render it indecipherable. While a standard SIM card will skip this step, it is a standard feature with all VipLine SIM cards. When you hang up, your correspondent will be incapable of calling you back or searching their logs for your number.
A feature ideal for occupations where a tracked location could be hazardous is geolocation masking. When you use your mobile device with a VipLine SIM card, you can guarantee that your service provider will never know your location. Using a secure USSD (Unstructured Supplementary Service Data) channel, VipLine masks your location and keeps any geographic data safe.
Your voice is a unique identifier and can easily publicize more information about yourself. If you are worried about this threat, the VipLine SIM card has you covered. With the option to select this option when needed, our tech will alter your voice’s phonetic characteristics so they are unrecognizable.
Unlike most GSM providers who require commitment in writing, VipLine offers its features contract-less. Contracts can instill distrust in customers, which is why VipLine eliminates the risk by offering pre-paid anonymous SIM cards that never leave a paper trail. Not even we will know your name.

You can take advantage of all the VipLine features with the simple click of a button.
Take The Steps